Only 4% of organizations don’t use any third-party apps. For the whopping 96% that do, an effective third-party risk management strategy with third-party risk management metrics is essential.
Third-party risk management metrics (TPRM) help organizations understand whether or not their strategy is working. Moreover, the right metrics can assure the board that third parties aren’t introducing risk or, if they are, that their cybersecurity team is equipped to mitigate them. The challenge is selecting metrics meaningful to the security team and metrics that the board (more than likely a non-security audience) can truly appreciate.
Here’s what organizations need to know about third-party risk management metrics to create impactful reports for the board.
How Do You Assess Third-Party Risk?
Though third-party risk management starts with onboarding, it’s much more than that. Effective TPRM requires understanding every step of the third-party lifecycle, from the day they first access your organization to the day they no longer need it.
This includes evaluating what level of access they need and creating guidelines for where and how to access company systems and processes for revoking access once their relationship with the organization ends. Creating an effective third-party risk management strategy and then introducing metrics to evaluate performance would be best.
What Are Metrics for Third-Party Risk Management?
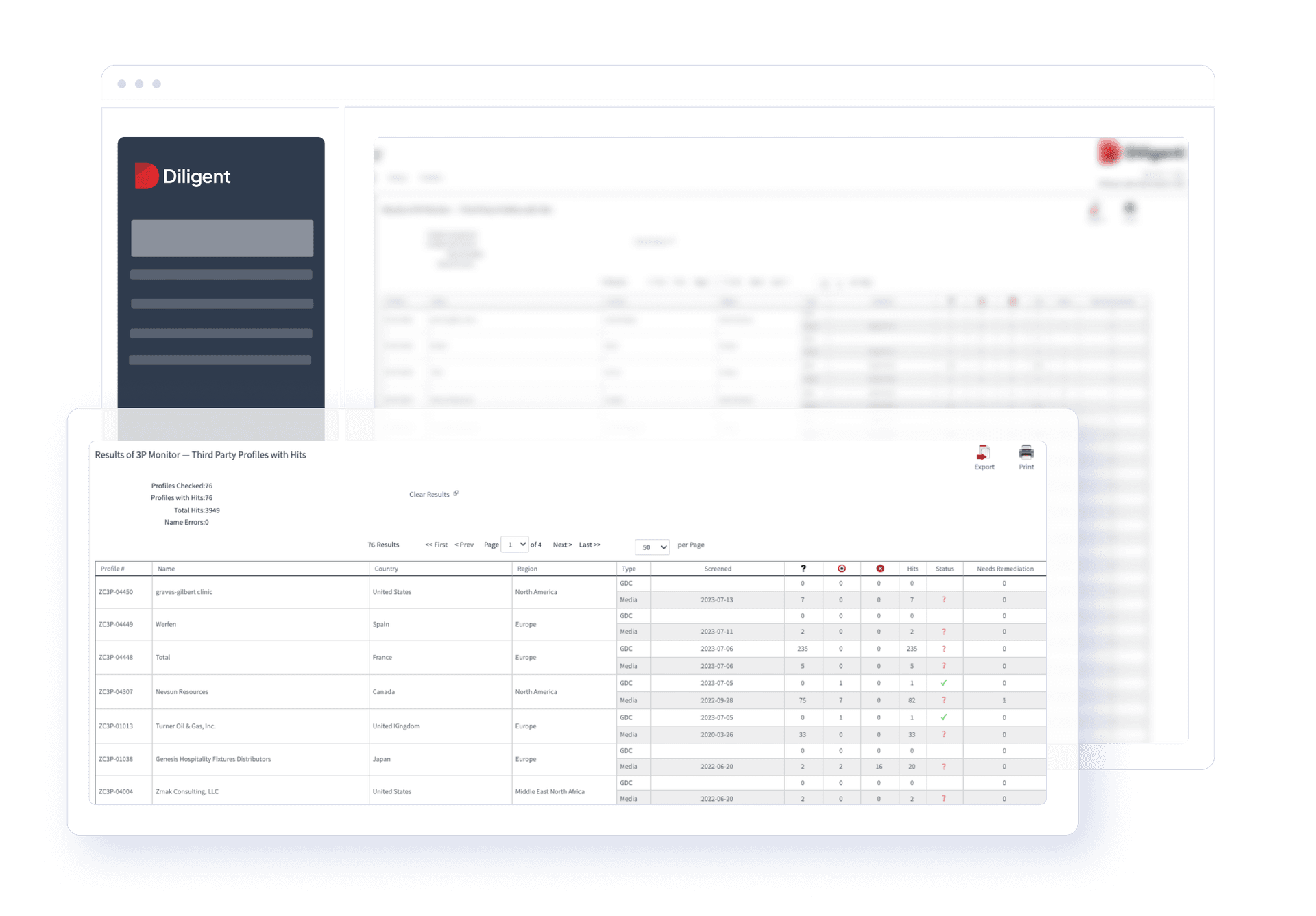
Third-party risk management metrics vary from organization to organization. A company that works heavily with contractors may need to evaluate different risks than an organization primarily using third-party apps. Regardless of the risk, it’s important to remember that the metrics should tell the organization’s risk story, illustrating what risks exist and how effective it is at mitigating them.
Some examples of risk management metrics are:
- Number of risks identified: This KPI measures how many risks the team (and individual employees) identifies over time. The organization’s objective will likely be to increase this number; the higher the number, the more influential the team is in understanding third-party risks.
- Number of risks that occurred: Identifying risks is excellent. But reducing the number of risks that come to fruition is, perhaps, even more important. A high number of risks identified coupled with a reduced number of risks that occurred can be a sign of an effective risk team.
- Cost of risk management: Reporting on this KPI should be two-fold; teams should be able to articulate the current cost of risk management and show how they’re reducing costs over time. This can be a great way to prove the team’s success since lower costs signal fewer risks over time.
- Time to detect: This KPI articulates how long it takes for a team to detect a possible risk. Boards will want low detection times, so risk managers should also report how their team has reduced (and will reduce) their detection time.
- Time to mitigation: Once teams have detected risks, they must mitigate them. Acting fast can save organizations from further financial and reputational damage. Time to mitigation can help teams visualize how quickly they are now and set objectives for increasing their speed over time.
- Comparison by business unit: Risk typically isn’t confined to a single business unit or division. Comparing KPIs between business units can help the board visualize where they’re most at risk and then prioritize risk management activities accordingly.
How to Choose Risk-Management Metrics
There’s more than one way to report on third-party risks effectively. Metrics depend on how an organization works with third parties and the risks they introduce, so no two organizations will report to their boards in precisely the same way. How a risk team reports to the board is heavily influenced by how security-savvy the board is. Less savvy boards may need more straightforward metrics than boards that already understand risk measurements.
But even if the metrics vary, organizations can take the same steps to choose which risk management metrics are right for them.
Here’s how:
- Understand each business unit: Risk managers and their teams need a deep understanding of each business unit and how they partner with third parties. Do they use third-party contractors or third-party apps? How do those third parties play into that business unit’s day-to-day activities? Risk teams should talk to key stakeholders within the business to get a complete insight into the business’s requirements.
- Create a risk program: Risk teams should use insights from each business unit to create a more standard risk program. The outcomes for each team may vary slightly, but this program should detail the organization’s requirements for managing third-party risk at each step of the third-party process.
- Use the right tools & technology: Managing risk is challenging. The more third parties an organization works with, the harder it is to identify and mitigate every risk. Third-party risk management software can do much of the heavy lifting, from enforcing third-party requirements to flagging emerging risks. The right tools can even help report to the board, creating a seamless, end-to-end third-party risk management process.
Third-Party Risk Metrics Support the TPRM Lifecycle
TPRM is circular. Just like risks evolve, so should the organization’s approach to identifying and mitigating them. In this way, third-party risk metrics are a critical part of the TPRM lifecycle. From onboarding to offboarding, organizations need metrics to understand the risks they face and whether or not their teams are becoming more efficient.
Rather than setting processes or metrics in stone, organizations should look at these as a living, breathing part of their risk program that can change as the risk landscape does. This always-on approach allows metrics to mature along with the organization, ensuring that the organization remains competitive in the face of ever-changing risks.
